阿里云oss直传相关笔记
1.也是菜鸟一枚,新的项目直接上go,之前都是写php
遇到问题还是先baidu google 不行了再请教别人。尽量不耽误别人时间
进入主题 基本都是 官方文档 还有就是乱搜整理的
好多时候直接问别人是,自己还没有理清楚流程,清楚了流程一步步就简单了。
还是要多动动自己的脑袋
一。前端直传 先看下简单流程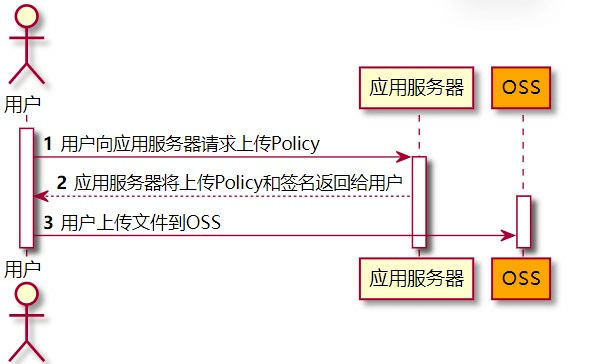
主要就是完成 2写个接口
代码如下:(自己看着删减)⚠️: 因为是前端直传 跨域 记得在oss里设置下
package app
import (
"crypto"
"crypto/hmac"
"crypto/rsa"
"crypto/sha1"
"crypto/x509"
"encoding/base64"
"encoding/json"
"encoding/pem"
"fmt"
"github.com/flipped-aurora/gin-vue-admin/server/model/common/response"
"github.com/gin-gonic/gin"
"hash"
"io"
"strconv"
"time"
)
type AppOssApi struct {
}
// 请填写您的AccessKeyId。
var accessKeyId string = ""
// 请填写您的AccessKeySecret。
var accessKeySecret string = ""
// host的格式为 bucketname.endpoint ,请替换为您的真实信息。
var host string = ""
// callbackUrl为 上传回调服务器的URL,请将下面的IP和Port配置为您自己的真实信息。
var callbackUrl string = ""
// 用户上传文件时指定的前缀。
var upload_dir string = "user-dir-prefix/"
var expire_time int64 = 30
const (
base64Table = "123QRSTUabcdVWXYZHijKLAWDCABDstEFGuvwxyzGHIJklmnopqr234560178912"
)
var coder = base64.NewEncoding(base64Table)
func base64Encode(src []byte) []byte {
return []byte(coder.EncodeToString(src))
}
func get_gmt_iso8601(expire_end int64) string {
var tokenExpire = time.Unix(expire_end, 0).UTC().Format("2006-01-02T15:04:05Z")
return tokenExpire
}
type ConfigStruct struct {
Expiration string `json:"expiration"`
Conditions [][]string `json:"conditions"`
}
type PolicyToken struct {
AccessKeyId string `json:"accessid"`
Host string `json:"host"`
Expire int64 `json:"expire"`
Signature string `json:"signature"`
Policy string `json:"policy"`
Directory string `json:"dir"`
Callback string `json:"callback"`
}
type CallbackParam struct {
CallbackUrl string `json:"callbackUrl"`
CallbackBody string `json:"callbackBody"`
CallbackBodyType string `json:"callbackBodyType"`
}
func (AppOssApi *AppOssApi) Get_policy_token(c *gin.Context) {
now := time.Now().Unix()
expire_end := now + expire_time
var tokenExpire = get_gmt_iso8601(expire_end)
//create post policy json
var config ConfigStruct
config.Expiration = tokenExpire
var condition []string
condition = append(condition, "starts-with")
condition = append(condition, "$key")
condition = append(condition, upload_dir)
config.Conditions = append(config.Conditions, condition)
//calucate signature
result, err := json.Marshal(config)
debyte := base64.StdEncoding.EncodeToString(result)
h := hmac.New(func() hash.Hash { return sha1.New() }, []byte(accessKeySecret))
io.WriteString(h, debyte)
signedStr := base64.StdEncoding.EncodeToString(h.Sum(nil))
var callbackParam CallbackParam
callbackParam.CallbackUrl = callbackUrl
callbackParam.CallbackBody = "filename=${object}&size=${size}&mimeType=${mimeType}&height=${imageInfo.height}&width=${imageInfo.width}"
callbackParam.CallbackBodyType = "application/x-www-form-urlencoded"
callback_str, err := json.Marshal(callbackParam)
if err != nil {
fmt.Println("callback json err:", err)
}
callbackBase64 := base64.StdEncoding.EncodeToString(callback_str)
var policyToken PolicyToken
policyToken.AccessKeyId = accessKeyId
policyToken.Host = host
policyToken.Expire = expire_end
policyToken.Signature = string(signedStr)
policyToken.Directory = upload_dir
policyToken.Policy = string(debyte)
policyToken.Callback = string(callbackBase64)
//response1, err := json.Marshal(policyToken)
//if err != nil {
// fmt.Println("json err:", err)
//}
//return string(response1)
response.AppOkWithData(policyToken, c)
//return response.AppOkWithMessage(string(response1), c)
}
/* VerifySignature
* VerifySignature需要三个重要的数据信息来进行签名验证: 1>获取公钥PublicKey; 2>生成新的MD5鉴权串; 3>解码Request携带的鉴权串;
* 1>获取公钥PublicKey : 从RequestHeader的"x-oss-pub-key-url"字段中获取 URL, 读取URL链接的包含的公钥内容, 进行解码解析, 将其作为rsa.VerifyPKCS1v15的入参。
* 2>生成新的MD5鉴权串 : 把Request中的url中的path部分进行urldecode, 加上url的query部分, 再加上body, 组合之后进行MD5编码, 得到MD5鉴权字节串。
* 3>解码Request携带的鉴权串 : 获取RequestHeader的"authorization"字段, 对其进行Base64解码,作为签名验证的鉴权对比串。
* rsa.VerifyPKCS1v15进行签名验证,返回验证结果。
* */
func verifySignature(bytePublicKey []byte, byteMd5 []byte, authorization []byte) bool {
pubBlock, _ := pem.Decode(bytePublicKey)
if pubBlock == nil {
fmt.Printf("Failed to parse PEM block containing the public key")
return false
}
pubInterface, err := x509.ParsePKIXPublicKey(pubBlock.Bytes)
if (pubInterface == nil) || (err != nil) {
fmt.Printf("x509.ParsePKIXPublicKey(publicKey) failed : %s \n", err.Error())
return false
}
pub := pubInterface.(*rsa.PublicKey)
errorVerifyPKCS1v15 := rsa.VerifyPKCS1v15(pub, crypto.MD5, byteMd5, authorization)
if errorVerifyPKCS1v15 != nil {
fmt.Printf("\nSignature Verification is Failed : %s \n", errorVerifyPKCS1v15.Error())
//printByteArray(byteMd5, "AuthMd5(fromNewAuthString)")
//printByteArray(bytePublicKey, "PublicKeyBase64")
//printByteArray(authorization, "AuthorizationFromRequest")
return false
}
fmt.Printf("\nSignature Verification is Successful. \n")
return true
}
func printByteArray(byteArrary []byte, arrName string) {
fmt.Printf("++++++++ printByteArray : ArrayName=%s, ArrayLength=%d \n", arrName, len(byteArrary))
for i := 0; i < len(byteArrary); i++ {
fmt.Printf("%02x", byteArrary[i])
}
fmt.Printf("\n-------- printByteArray : End . \n")
}
type EscapeError string
func (e EscapeError) Error() string {
return "invalid URL escape " + strconv.Quote(string(e))
}
type InvalidHostError string
func (e InvalidHostError) Error() string {
return "invalid character " + strconv.Quote(string(e)) + " in host name"
}
type encoding int
const (
encodePath encoding = 1 + iota
encodePathSegment
encodeHost
encodeZone
encodeUserPassword
encodeQueryComponent
encodeFragment
)
// unescapePath : unescapes a string; the mode specifies, which section of the URL string is being unescaped.
func unescapePath(s string, mode encoding) (string, error) {
// Count %, check that they're well-formed.
mode = encodePathSegment
n := 0
hasPlus := false
for i := 0; i < len(s); {
switch s[i] {
case '%':
n++
if i+2 >= len(s) || !ishex(s[i+1]) || !ishex(s[i+2]) {
s = s[i:]
if len(s) > 3 {
s = s[:3]
}
return "", EscapeError(s)
}
// Per https://tools.ietf.org/html/rfc3986#page-21
// in the host component %-encoding can only be used
// for non-ASCII bytes.
// But https://tools.ietf.org/html/rfc6874#section-2
// introduces %25 being allowed to escape a percent sign
// in IPv6 scoped-address literals. Yay.
if mode == encodeHost && unhex(s[i+1]) < 8 && s[i:i+3] != "%25" {
return "", EscapeError(s[i : i+3])
}
if mode == encodeZone {
// RFC 6874 says basically "anything goes" for zone identifiers
// and that even non-ASCII can be redundantly escaped,
// but it seems prudent to restrict %-escaped bytes here to those
// that are valid host name bytes in their unescaped form.
// That is, you can use escaping in the zone identifier but not
// to introduce bytes you couldn't just write directly.
// But Windows puts spaces here! Yay.
v := unhex(s[i+1])<<4 | unhex(s[i+2])
if s[i:i+3] != "%25" && v != ' ' && shouldEscape(v, encodeHost) {
return "", EscapeError(s[i : i+3])
}
}
i += 3
case '+':
hasPlus = mode == encodeQueryComponent
i++
default:
if (mode == encodeHost || mode == encodeZone) && s[i] < 0x80 && shouldEscape(s[i], mode) {
return "", InvalidHostError(s[i : i+1])
}
i++
}
}
if n == 0 && !hasPlus {
return s, nil
}
t := make([]byte, len(s)-2*n)
j := 0
for i := 0; i < len(s); {
switch s[i] {
case '%':
t[j] = unhex(s[i+1])<<4 | unhex(s[i+2])
j++
i += 3
case '+':
if mode == encodeQueryComponent {
t[j] = ' '
} else {
t[j] = '+'
}
j++
i++
default:
t[j] = s[i]
j++
i++
}
}
return string(t), nil
}
// Please be informed that for now shouldEscape does not check all
// reserved characters correctly. See golang.org/issue/5684.
func shouldEscape(c byte, mode encoding) bool {
// §2.3 Unreserved characters (alphanum)
if 'A' <= c && c <= 'Z' || 'a' <= c && c <= 'z' || '0' <= c && c <= '9' {
return false
}
if mode == encodeHost || mode == encodeZone {
// §3.2.2 Host allows
// sub-delims = "!" / "$" / "&" / "'" / "(" / ")" / "*" / "+" / "," / ";" / "="
// as part of reg-name.
// We add : because we include :port as part of host.
// We add [ ] because we include [ipv6]:port as part of host.
// We add < > because they're the only characters left that
// we could possibly allow, and Parse will reject them if we
// escape them (because hosts can't use %-encoding for
// ASCII bytes).
switch c {
case '!', '$', '&', '\'', '(', ')', '*', '+', ',', ';', '=', ':', '[', ']', '<', '>', '"':
return false
}
}
switch c {
case '-', '_', '.', '~': // §2.3 Unreserved characters (mark)
return false
case '$', '&', '+', ',', '/', ':', ';', '=', '?', '@': // §2.2 Reserved characters (reserved)
// Different sections of the URL allow a few of
// the reserved characters to appear unescaped.
switch mode {
case encodePath: // §3.3
// The RFC allows : @ & = + $ but saves / ; , for assigning
// meaning to individual path segments. This package
// only manipulates the path as a whole, so we allow those
// last three as well. That leaves only ? to escape.
return c == '?'
case encodePathSegment: // §3.3
// The RFC allows : @ & = + $ but saves / ; , for assigning
// meaning to individual path segments.
return c == '/' || c == ';' || c == ',' || c == '?'
case encodeUserPassword: // §3.2.1
// The RFC allows ';', ':', '&', '=', '+', '$', and ',' in
// userinfo, so we must escape only '@', '/', and '?'.
// The parsing of userinfo treats ':' as special so we must escape
// that too.
return c == '@' || c == '/' || c == '?' || c == ':'
case encodeQueryComponent: // §3.4
// The RFC reserves (so we must escape) everything.
return true
case encodeFragment: // §4.1
// The RFC text is silent but the grammar allows
// everything, so escape nothing.
return false
}
}
// Everything else must be escaped.
return true
}
func ishex(c byte) bool {
switch {
case '0' <= c && c <= '9':
return true
case 'a' <= c && c <= 'f':
return true
case 'A' <= c && c <= 'F':
return true
}
return false
}
func unhex(c byte) byte {
switch {
case '0' <= c && c <= '9':
return c - '0'
case 'a' <= c && c <= 'f':
return c - 'a' + 10
case 'A' <= c && c <= 'F':
return c - 'A' + 10
}
return 0
}
二:阿里云的STS临时授权
"github.com/aliyun/alibaba-cloud-sdk-go/services/sts"
type Res struct {
AccessKeyId string `json:"access_key_id"`
AccessKeySecret string `json:"access_key_secret"`
VisitPrefix string `json:"visit_prefix"`
FolderPath string `json:"folder_path"`
}
func (appUsersApi *AppUsersApi) Alisign(c *gin.Context) {
//构建一个阿里云客户端, 用于发起请求。
//设置调用者(RAM用户或RAM角色)的AccessKey ID和AccessKey Secret。
client, err := sts.NewClientWithAccessKey("cn-hangzhou", "", "")
//构建请求对象。
request := sts.CreateAssumeRoleRequest()
request.Scheme = "https"
//设置参数。关于参数含义和设置方法,请参见《API参考》。
roleArn := ""
request.RoleArn = roleArn
request.RoleSessionName = ""
//发起请求,并得到响应。
response1, err := client.AssumeRole(request)
if err != nil {
fmt.Print(err.Error())
}
//fmt.Printf("response is %#v\n", response)
var res = Res{
AccessKeyId: response1.Credentials.AccessKeyId,
AccessKeySecret: response1.Credentials.AccessKeySecret,
VisitPrefix: "",
FolderPath: "",
}
response.AppOkWithData(res, c)
}这个是文档地址:仔细研究
help.aliyun.com/document_detail/59...
本作品采用《CC 协议》,转载必须注明作者和本文链接



 关于 LearnKu
关于 LearnKu



